
Cybersecurity Blog
-

Third-Party Supply Chain Risk: A Challenge for Cybersecurity Professionals in Australia
The Growing Concern over Third-Party Supply Chain Risk Third-party supply chain risk has become a significant concern among Australian cyber…
-

WhatsApp Plans to Enable Screen Sharing for Collaborative Video Watching and Music Listening
Introduction to New WhatsApp Features One of Meta’s applications, WhatsApp, continues to develop new features set to improve online communication…
-
Amidst Explosive Expansion, Nigerian TikTok Community Faces Content Deletions Due to Nudity and Hateful Conduct
“`markdown Overview of TikTok’s Community Guidelines Enforcement Report In December, TikTok released its Community Guidelines Enforcement Report detailing the content…
-

Honor 90 GT Launches with Snapdragon 8 Gen 2 and up to 24GB RAM
Introduction of the Honor 90 GT Honor has unveiled its latest flagship contender in the Chinese market, the Honor 90…
-
Four Out of Five Downloads of Apache Struts 2 Are for Versions Containing a Critical Vulnerability
Developers Neglecting Critical RCE Vulnerability in Apache Struts Security vendor Sonatype has raised concerns that developers are overlooking a critical…
-
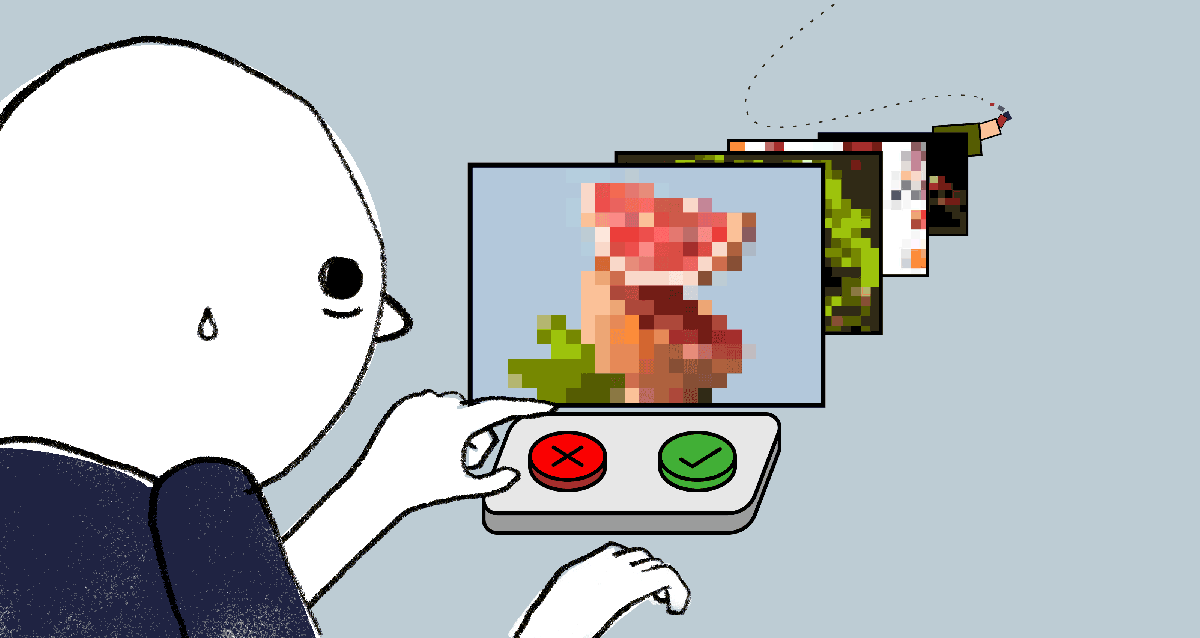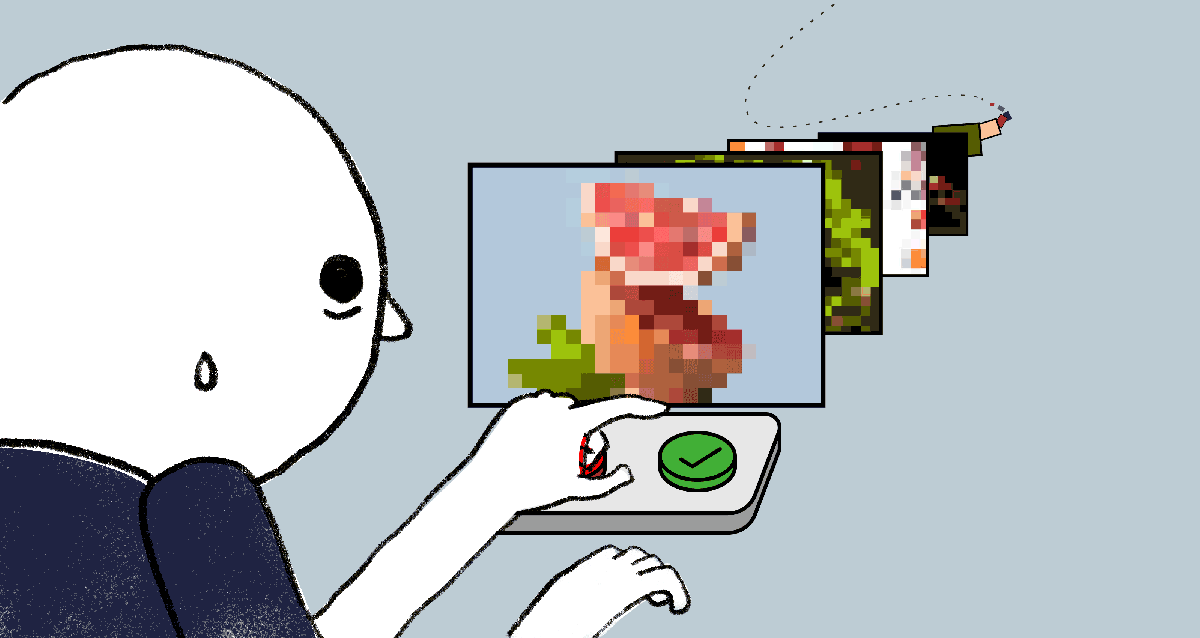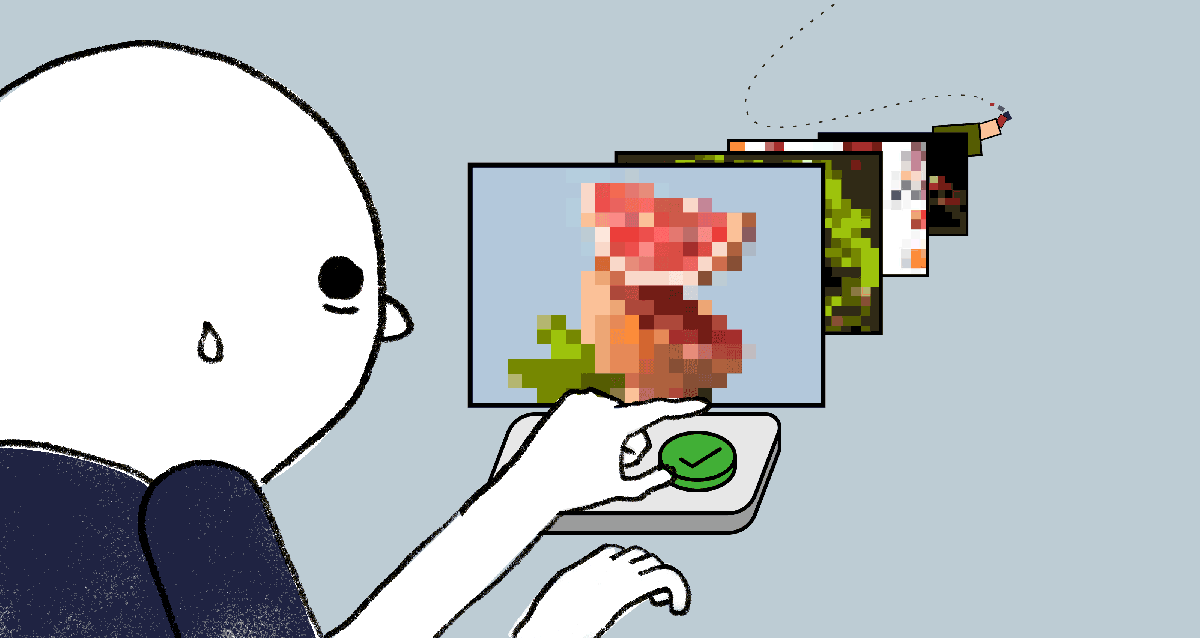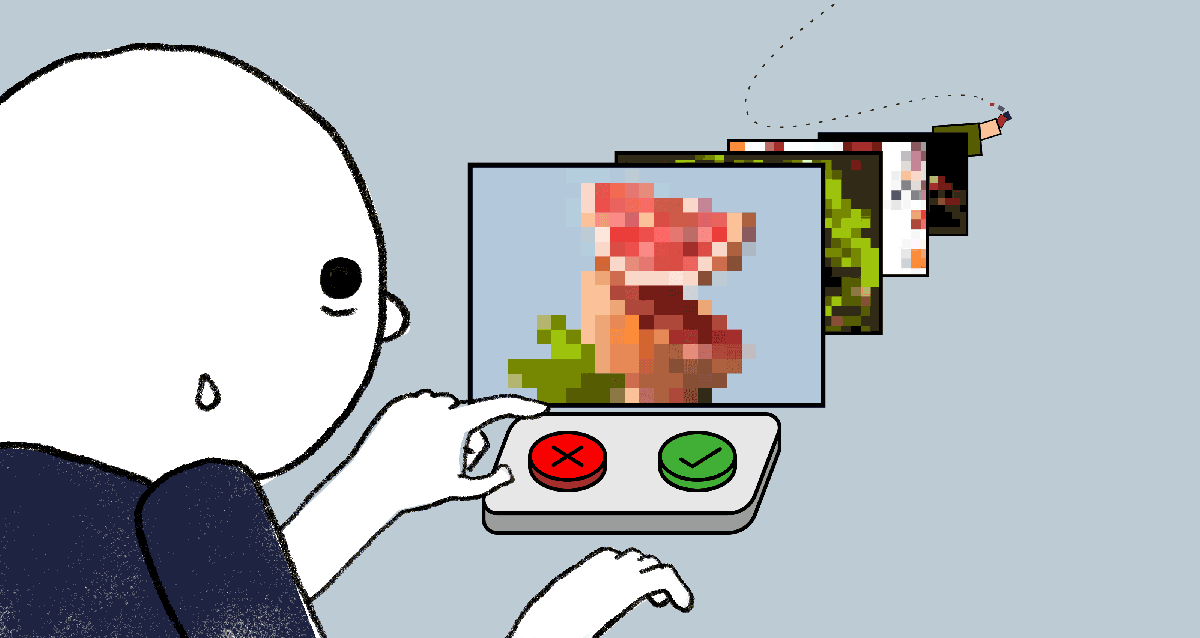
Y Combinator-Backed Intrinsic Develops Infrastructure for Trust and Safety Teams
Meeting of Minds at Apple’s Fraud Engineering Team A few years ago, engineers Karine Mellata and Michael Lin teamed up…
-

The 8 Best Video Games of 2023
Rediscovering Classic Worlds in 2023’s Best Video Games The year 2023 in video gaming was marked by a trend of…
-

The Best Tablet of 2023
Unfortunately, it seems there has been a mistake or a misunderstanding. As an AI with a knowledge cutoff in April…
-
How Durable is the nubia Red Magic 9 Pro? The Gaming Smartphone Aces JerryRigEverything’s Durability Test (Video)
Global Launch of Red Magic 9 Pro Gaming Smartphone A few days ago, Nubia globally launched its latest addition to…
